Sharpen Your Knowledge with Trend (Deep-Security-Professional) Certification Sample Questions
CertsTime has provided you with a sample question set to elevate your knowledge about the Trend Micro Certified Professional for Deep Security Exam . With these updated sample questions, you can become quite familiar with the difficulty level and format of the real Deep-Security-Professional certification test. Try our sample Trend Micro Certified Professional for Deep Security Exam certification practice exam to get a feel for the real exam environment. Our sample practice exam gives you a sense of reality and an idea of the questions on the actual Trend Micro Certified Professional for Deep Security certification exam.
Our sample questions are similar to the Real Trend Deep-Security-Professional exam questions. The premium Trend Micro Certified Professional for Deep Security Exam certification practice exam gives you a golden opportunity to evaluate and strengthen your preparation with real-time scenario-based questions. Plus, by practicing real-time scenario-based questions, you will run into a variety of challenges that will push you to enhance your knowledge and skills.
Trend Deep-Security-Professional Sample Questions:
The maximum disk space limit for the Identified Files folder is reached. What is the expected Deep Security Agent behavior in this scenario?
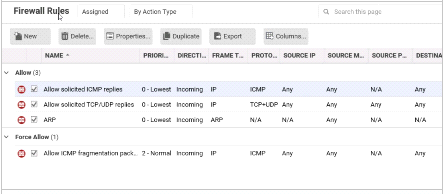
While viewing the details of the Firewall Protection Module, as displayed in the exhibit, you note that a few rules have already been assigned. You try to disable these rules, but they can not be unassigned. Why can the displayed rules not be unassigned?
Recommendation scans can detect applications and/or vulnerabilities on servers on the network. Which of the following Protection Modules make use of Recommendation scans?
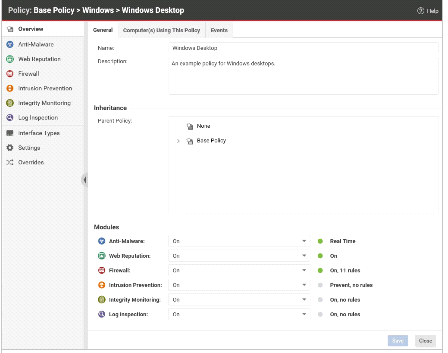
When viewing the details for a policy, as displayed in the exhibit, you notice that the Application Control Protection Module is not available. In this example, why would this Protection Modules not be available?
Which of the following correctly identifies the order of the steps used by the Web Reputation Protection Module to determine if access to a web site should be allowed?
Note: If there is any error in our Trend Deep-Security-Professional certification exam sample questions, please update us via email at support@certstime.com.



 Try Before You Buy!
Try Before You Buy!