Sharpen Your Knowledge with GAQM CEH (CPEH-001) Certification Sample Questions
CertsTime has provided you with a sample question set to elevate your knowledge about the GAQM Certified Professional Ethical Hacker (CPEH) Exam . With these updated sample questions, you can become quite familiar with the difficulty level and format of the real CPEH-001 certification test. Try our sample GAQM Certified Professional Ethical Hacker (CPEH) Exam certification practice exam to get a feel for the real exam environment. Our sample practice exam gives you a sense of reality and an idea of the questions on the actual GAQM Certified Ethical Hacker certification exam.
Our sample questions are similar to the Real GAQM CEH CPEH-001 exam questions. The premium GAQM Certified Professional Ethical Hacker (CPEH) Exam certification practice exam gives you a golden opportunity to evaluate and strengthen your preparation with real-time scenario-based questions. Plus, by practicing real-time scenario-based questions, you will run into a variety of challenges that will push you to enhance your knowledge and skills.
GAQM CPEH-001 Sample Questions:
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
Exhibit:
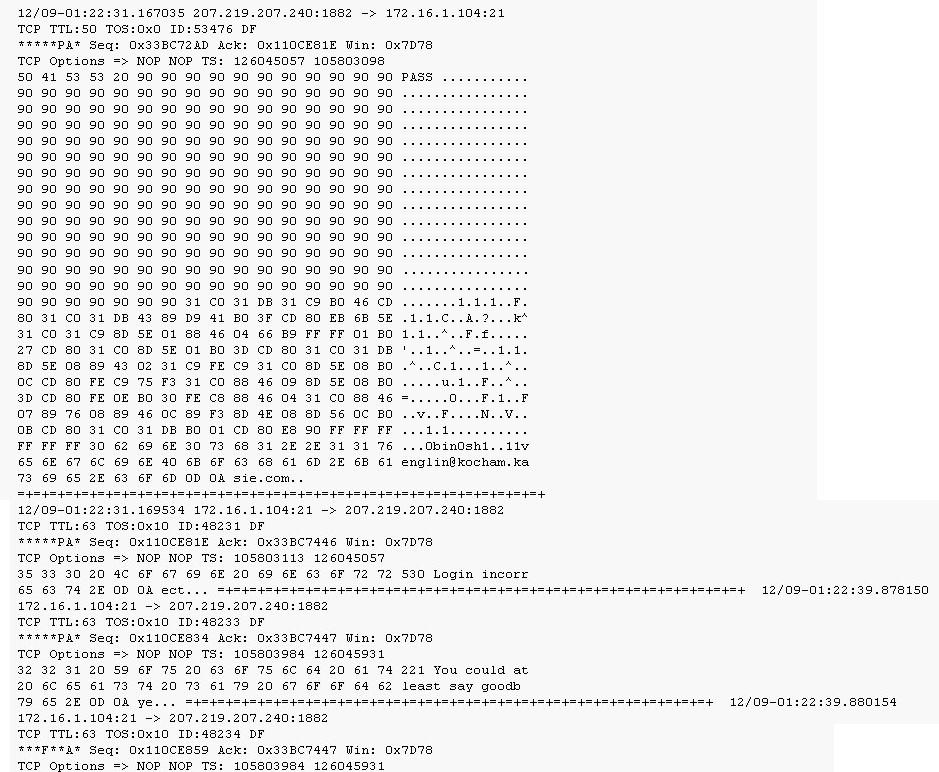
Given the following extract from the snort log on a honeypot, what do you infer from the attack?
A program that defends against a port scanner will attempt to:
John has a proxy server on his network which caches and filters web access. He shuts down all unnecessary ports and services. Additionally, he has installed a firewall (Cisco PIX) that will not allow users to connect to any outbound ports. Jack, a network user has successfully connected to a remote server on port 80 using netcat. He could in turn drop a shell from the remote machine. Assuming an attacker wants to penetrate John's network, which of the following options is he likely to choose?
Basically, there are two approaches to network intrusion detection: signature detection, and anomaly detection. The signature detection approach utilizes well-known signatures for network traffic to identify potentially malicious traffic. The anomaly detection approach utilizes a previous history of network traffic to search for patterns that are abnormal, which would indicate an intrusion. How can an attacker disguise his buffer overflow attack signature such that there is a greater probability of his attack going undetected by the IDS?
Note: If there is any error in our GAQM CPEH-001 certification exam sample questions, please update us via email at support@certstime.com.



 Try Before You Buy!
Try Before You Buy!