Sharpen Your Knowledge with Eccouncil ECSA (ECSAv10) Certification Sample Questions
CertsTime has provided you with a sample question set to elevate your knowledge about the Eccouncil Certified Security Analyst (ECSA) v10 exam. With these updated sample questions, you can become quite familiar with the difficulty level and format of the real ECSAv10 certification test. Try our sample Eccouncil Certified Security Analyst (ECSA) v10 certification practice exam to get a feel for the real exam environment. Our sample practice exam gives you a sense of reality and an idea of the questions on the actual Eccouncil EC-Council Certified Security Analyst certification exam.
Our sample questions are similar to the Real Eccouncil ECSA ECSA v10 ECSAv10 exam questions. The premium Eccouncil Certified Security Analyst (ECSA) v10 certification practice exam gives you a golden opportunity to evaluate and strengthen your preparation with real-time scenario-based questions. Plus, by practicing real-time scenario-based questions, you will run into a variety of challenges that will push you to enhance your knowledge and skills.
Eccouncil ECSAv10 Sample Questions:
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
An external intrusion test and analysis identify security weaknesses and strengths of the client's systems and networks as they appear from outside the client's security perimeter, usually from the Internet.
The goal of an external intrusion test and analysis is to demonstrate the existence of known vulnerabilities that could be exploited by an external attacker.
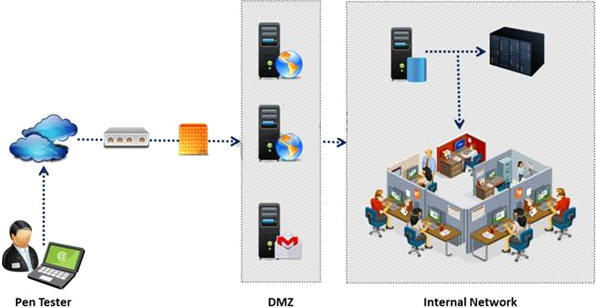
During external penetration testing, which of the following scanning techniques allow you to determine a port's state without making a full connection to the host?
Today, most organizations would agree that their most valuable IT assets reside within applications and databases. Most would probably also agree that these are areas that have the weakest levels of security, thus making them the prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers.
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card numbers, SSNs, and other authentication credentials?
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteri
a. If it does, it is routed between the networks, otherwise it is stopped.
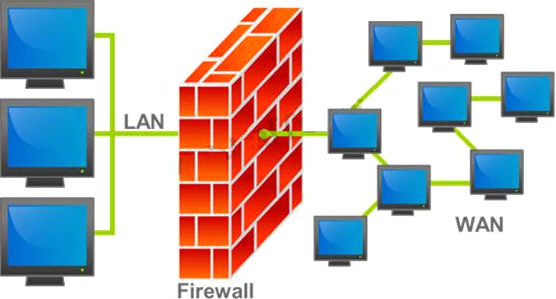
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
include
#include
int main(int argc, char *argv[])
{
char buffer[10];
if (argc < 2)
{
fprintf(stderr, "USAGE: %s string\n", argv[0]);
return 1;
}
strcpy(buffer, argv[1]);
return 0;
}
Note: If there is any error in our Eccouncil ECSAv10 certification exam sample questions, please update us via email at support@certstime.com.



 Try Before You Buy!
Try Before You Buy!