Sharpen Your Knowledge with Cisco (300-215) Certification Sample Questions
CertsTime has provided you with a sample question set to elevate your knowledge about the Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies exam. With these updated sample questions, you can become quite familiar with the difficulty level and format of the real 300-215 certification test. Try our sample Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies certification practice exam to get a feel for the real exam environment. Our sample practice exam gives you a sense of reality and an idea of the questions on the actual Cisco Certified CyberOps Professional certification exam.
Our sample questions are similar to the Real Cisco CBRFIR 300-215 exam questions. The premium Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies certification practice exam gives you a golden opportunity to evaluate and strengthen your preparation with real-time scenario-based questions. Plus, by practicing real-time scenario-based questions, you will run into a variety of challenges that will push you to enhance your knowledge and skills.
Cisco 300-215 Sample Questions:
An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team's approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?
Refer to the exhibit.
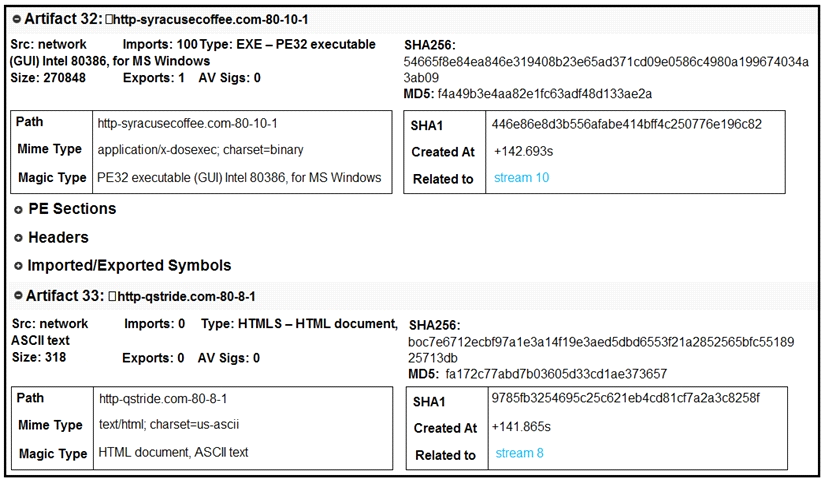
What do these artifacts indicate?
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
Which magic byte indicates that an analyzed file is a pdf file?
Refer to the exhibit.
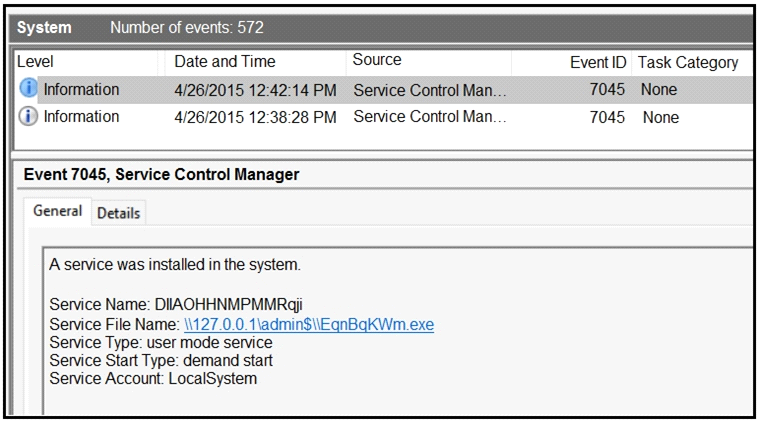
An HR department submitted a ticket to the IT helpdesk indicating slow performance on an internal share server. The helpdesk engineer checked the server with a real-time monitoring tool and did not notice anything suspicious. After checking the event logs, the engineer noticed an event that occurred 48 hour prior. Which two indicators of compromise should be determined from this information? (Choose two.)
Note: If there is any error in our Cisco 300-215 certification exam sample questions, please update us via email at support@certstime.com.



 Try Before You Buy!
Try Before You Buy!