Sharpen Your Knowledge with Cisco (350-201) Certification Sample Questions
CertsTime has provided you with a sample question set to elevate your knowledge about the Cisco Performing CyberOps Using Core Security Technologies exam. With these updated sample questions, you can become quite familiar with the difficulty level and format of the real 350-201 certification test. Try our sample Cisco Performing CyberOps Using Core Security Technologies certification practice exam to get a feel for the real exam environment. Our sample practice exam gives you a sense of reality and an idea of the questions on the actual Cisco Certified CyberOps Professional certification exam.
Our sample questions are similar to the Real Cisco CBRCOR 350-201 exam questions. The premium Cisco Performing CyberOps Using Core Security Technologies certification practice exam gives you a golden opportunity to evaluate and strengthen your preparation with real-time scenario-based questions. Plus, by practicing real-time scenario-based questions, you will run into a variety of challenges that will push you to enhance your knowledge and skills.
Cisco 350-201 Sample Questions:
Refer to the exhibit.
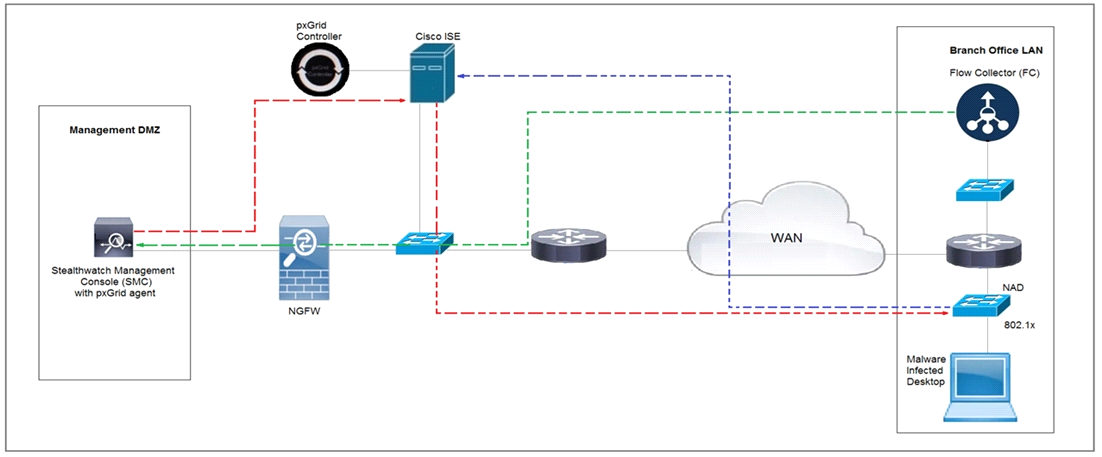
Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy. Which method was used to signal ISE to quarantine the endpoints?
Which bash command will print all lines from the ''colors.txt'' file containing the non case-sensitive pattern ''Yellow''?
An engineer detects an intrusion event inside an organization's network and becomes aware that files that contain personal data have been accessed. Which action must be taken to contain this attack?
A security manager received an email from an anomaly detection service, that one of their contractors has downloaded 50 documents from the company's confidential document management folder using a company- owned asset al039-ice-4ce687TL0500. A security manager reviewed the content of downloaded documents and noticed that the data affected is from different departments. What are the actions a security manager should take?
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
Note: If there is any error in our Cisco 350-201 certification exam sample questions, please update us via email at support@certstime.com.



 Try Before You Buy!
Try Before You Buy!